How to Using Vinetto 0.06 (r56)
This is part of the Digital Forensics section of BT2 and 3
Note: If using BT3 and this tool doesn't work then please see the thread here: [url=http://forums.remote-exploit.org/showthread.php?t=10744]Possible bug[/url]
Some Background: Vinetto is a forensics tool to examine Thumbs.db files.It is a command line python script that works on Linux, Mac OS X and Cygwin(win32).
Source: [url=http://vinetto.sourceforge.net/]Vinetto[/url]
Disclaimer: This information is for educational purposes only and not to commit a crime.
If you do something that causes you to hose your box don't come kicking and screaming on the forums!
OK you may be asking your self "why would I need this tool?" This tool and the whole "forensics section" of BT is one that the average person is not going to use. Now on the other hand if you conduct forensics investigation as either some type of "police official" or as a pen tester, then this tool can come in very handy for you.
Now there are other tools that can do the same basic thing however if you need it it's included.
NOTE: When doing any type of forensic work it is imperative that we do not damage the target computer in any way. Having said that we should boot our BT disk over our target computer using the "bt nohd" boot option. If you don't know what this means then stop here and go read about it here: [url=http://backtrack.offensive-security.com/index.php/Cheats]Cheats[/url]
Ok in order to get this to work we need to go to the command line or alternatively through K>Backtrack>Digital Forensics>All>Vinetto
Now lets have a look at the options that are presented when we do a --help
[code] bt ~ # vinetto --help
usage: vinetto [OPTIONS] [-o DIR] file
options:
--version show program's version number and exit
-h, --help show this help message and exit
-o DIR write thumbnails to DIR
-H write html report to DIR [/code]
Now the output shows us only two useful switches -o will write our thumbnail to a given directory and the -H creates a html report to a directory
and these two can be combined like so -Ho this will give us both the thumbs and and report in html format. This is useful if we have a lot of thumbs to go through.
So far so good right? OK now for my example usage.
I booted BT over my laptop that has Windblows XP next I opened a shell and did a:
[code]# find / -name Thumbs.db
/mnt/hda1/Program Files/Windows NT/Thumbs.db
/mnt/hda1/RECYCLER/Thumbs.db
/mnt/hda1/WINDOWS/Thumbs.db
/mnt/hda1/Program Files/Microsoft Office Old/Office/Bitmaps/Dbwiz/Thumbs.db
bt ~ #
[/code]
The above is a truncated version of the output, yours will be different. Our target file will be the last one, the "/Dbwiz/Thumbs.db"
So now you need to setup a storage device of some sort I used a usb stick seems to be the easiest. now go ahead and mount it and make a directory in it.
I used "thumbs" for mine. Ok now we have both a target directory and a "save location" we can go ahead and extract our thumbs to it.
so in a shell again give:
[code vinetto -Ho /mnt/sda1_removable/thumbs "/mnt/hda1/Program Files/Microsoft Office Old/Office/Bitmaps/Dbwiz/Thumbs.db"
** Warning: Cannot find "Image" module.
Vinetto will only extract Type 2 thumbnails.
Root Entry modify timestamp : Tue Apr 4 02:15:03 2006
------------------------------------------------------
0001 Mon Mar 22 01:00:00 1999 ORDPROC.GIF
0002 Mon Mar 22 01:00:00 1999 ASSETS.GIF
0003 Mon Mar 22 01:00:00 1999 CONTACTS.GIF
0004 Mon Mar 22 01:00:00 1999 EVTMGMT.GIF
0005 Mon Mar 22 01:00:00 1999 EXPENSES.GIF
0006 Mon Mar 22 01:00:00 1999 INVENTRY.GIF
0007 Mon Mar 22 01:00:00 1999 LEDGER.GIF
------------------------------------------------------
7 Type 2 thumbnails extracted to /mnt/sda1_removable/thumbs/
[/code]
hit enter and you should see the same basic output as above.
This show use the thumbs that we have recovered and the time they were created on our target and as well as their respective names.
Now we can go to our "save location" to verify our files are there. Also check out the .html output file as this is easier to manage then all of the other files.
I have posted some photos of the output if you need look at them [url=http://picasaweb.google.com/Archangel.Amael/VinettoTutorial]VinettoOutput[/url]
And that's it, a simple program that can help if you need it.
Please leave some feedback if this helped or hindered you, Thanks :)
NOTE: Credit to the author of this tool and to the authors of the [url=http://www.amazon.com/Penetration-Testers-Open-Source-Toolkit/dp/1597492132/ref=sr_1_1?ie=UTF8&s=books&qid=1198971560&sr=1-1]THE BOOK[/url]
This is where I got most of the information from as well as the vinetto website.
I did find in my experiments that you need to use the flags as "-Ho" and not "-oH" doing so I got a "vinetto: error: incorrect number of arguments" error each time.

Custom Search
Thursday, September 25, 2008
Sunday, September 21, 2008
Adding 'Command Prompt Here' to explorer
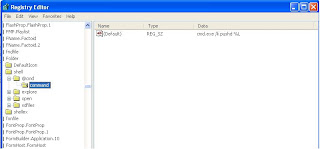
 Open regedit, and navigate to HKEY_LOCAL_MACHINE/Software/Classes/Folder/Shell. Make a new key called 'Command Prompt' and set the default key to whatever you want listed in the menu. Inside that key make another key named 'command' and set the default string to
Open regedit, and navigate to HKEY_LOCAL_MACHINE/Software/Classes/Folder/Shell. Make a new key called 'Command Prompt' and set the default key to whatever you want listed in the menu. Inside that key make another key named 'command' and set the default string tocmd.exe /k pushd %L Close regedit, right click on a folder and you should now have a new right click menu with a shortcut used to open a command prompt window to that folder. resource - http://r00tsecurity.org/forums/lofiversion/index.php/t4917.html
Thursday, September 11, 2008
Configuration for Oracle Form 10g, so you can build a page
#This is added for /oracle/product/10.1.2/midr2/forms/server/formsweb.cfg
#
# main config# URL like "http://serverip:8889/forms/frmservlet?config=xxx".
[xxx]
separateFrame=True
lookandfeel=Generic
width=800
height=650
form=LOGINDC.fmx
userid=user/passwd@dcdb
workingDirectory=/oracle/product/10.1.2/midr2/forms
#
# main config# URL like "http://serverip:8889/forms/frmservlet?config=xxx".
[xxx]
separateFrame=True
lookandfeel=Generic
width=800
height=650
form=LOGINDC.fmx
userid=user/passwd@dcdb
workingDirectory=/oracle/product/10.1.2/midr2/forms
Removing SSO from Oracle Report 10g
11.3.1 Enabling and Disabling OracleAS Single Sign-On
To take advantage of OracleAS Single Sign-On out-of-the-box, the SINGLESIGNON parameter in the Reports Servlet configuration file (rwservlet.properties) is set to YES, which indicates that you will use OracleAS Single Sign-On to authenticate users. You may change this parameter to NO, if you choose not to use OracleAS Single Sign-On. If you choose NO, the Reports Server authenticates users by itself. The rwservlet configuration file is usually found in:
ORACLE_HOME\reports\conf
The SINGLESIGNON value is usually commented out after installation, but the default value is YES.
Note:
OracleAS Reports Services is configured for OracleAS Single Sign-On out-of-the-box. Oracle considers this to be the normal security deployment model and you should only turn it off if you plan to run in a completely custom security configuration.
11.3.2 Enabling and Disabling Reports Server Security
Reports Server security is turned on and off in the Reports Server configuration file. By default, the Reports Server configuration file, ORACLE_HOME/reports/conf/servername.conf, contains a security element like the following:
Note:
In releases prior to Oracle Reports 10g, the securityUserid property was specified differently. In Oracle Reports 10g and later releases, the old property specification is still provided but commented out.
This security element is referenced by default from the two default job elements in the configuration file to indicate that Reports Server security should be enforced:
To disable Reports Server security, you must remove or comment the security element as well as the
To take advantage of OracleAS Single Sign-On out-of-the-box, the SINGLESIGNON parameter in the Reports Servlet configuration file (rwservlet.properties) is set to YES, which indicates that you will use OracleAS Single Sign-On to authenticate users. You may change this parameter to NO, if you choose not to use OracleAS Single Sign-On. If you choose NO, the Reports Server authenticates users by itself. The rwservlet configuration file is usually found in:
ORACLE_HOME\reports\conf
The SINGLESIGNON value is usually commented out after installation, but the default value is YES.
Note:
OracleAS Reports Services is configured for OracleAS Single Sign-On out-of-the-box. Oracle considers this to be the normal security deployment model and you should only turn it off if you plan to run in a completely custom security configuration.
11.3.2 Enabling and Disabling Reports Server Security
Reports Server security is turned on and off in the Reports Server configuration file. By default, the Reports Server configuration file, ORACLE_HOME/reports/conf/servername.conf, contains a security element like the following:
Note:
In releases prior to Oracle Reports 10g, the securityUserid property was specified differently. In Oracle Reports 10g and later releases, the old property specification is still provided but commented out.
This security element is referenced by default from the two default job elements in the configuration file to indicate that Reports Server security should be enforced:
To disable Reports Server security, you must remove or comment the security element as well as the
Subscribe to:
Comments (Atom)